Token-based authentication is a system wherein users present their identification details in exchange for a unique access token. This token empowers them to access a web service, application, or other digital platforms within its validity period, negating the need for constant re-entry of their credentials.
The Dynamics of Token-Based Authentication
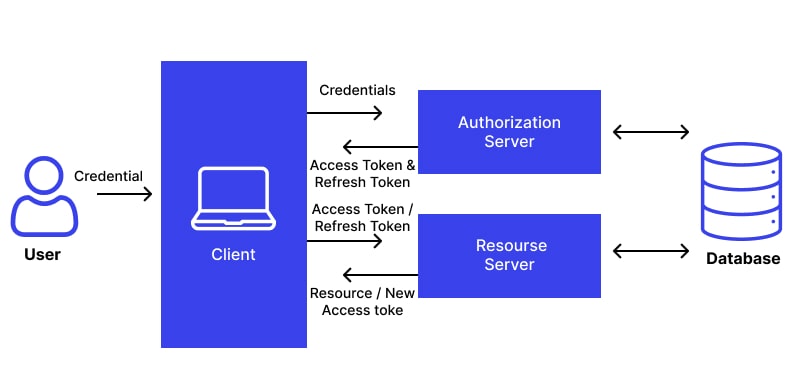
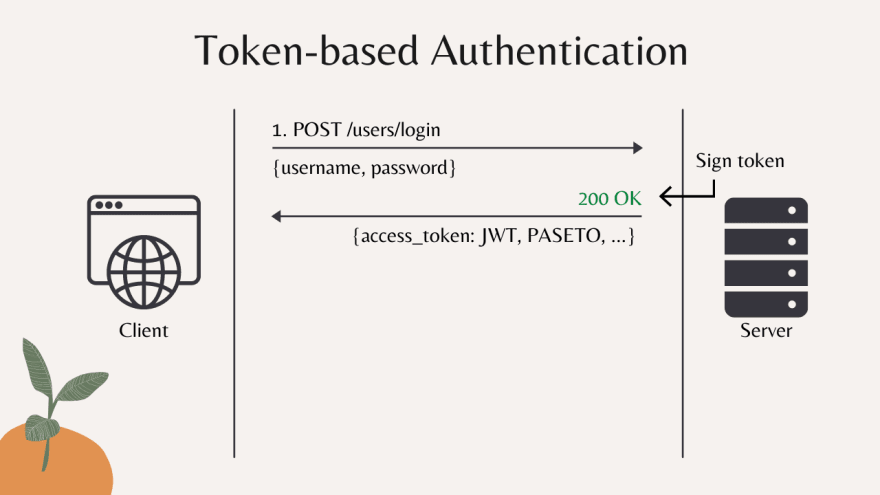
Everything kicks off when a user attempts to log into a particular digital environment, commonly using a password or other protective barriers. After validating the user’s data, an authorization entity dispenses an access token—a compact piece of information enabling the client software to safely communicate with the API server.
The entire process might seem intricate, but with the right resources and guides, such as implementing Token access, it becomes a lot simpler and more secure.
This strategy works by providing the server with an alternative, highly reliable avenue to verify a user’s identity and the legitimacy of a request.
Once the token-based mechanism is activated, the token acts much like a VIP pass. Users enjoy uninterrupted engagement with relevant platforms without continual authentication, up until the token reaches its expiration. This usually aligns with the user departing the platform or after a specific duration has elapsed.
The Benefits of Token-Based Authentication
There are manifold advantages to using token-based authentication:
- User-Friendly Experience: Users don’t need to input their credentials or undergo repeated verifications every instance they engage with an application or site. They enjoy uninterrupted access for the duration of the token’s validity.
- Augmented Digital Safeguarding: Token authentication fortifies the security layers beyond just the regular password or system-authentication methods. Generally, tokens pose a greater challenge to potential cyber threats than passwords.
- Precision in Oversight: It empowers system administrators with more refined control and oversight over each user activity.
- Minimized System Load: The token creation and its verification can be decoupled. Secondary services, like those from Entrust, can handle verification tasks, alleviating pressure on primary servers.
What Exactly is an Access Token?
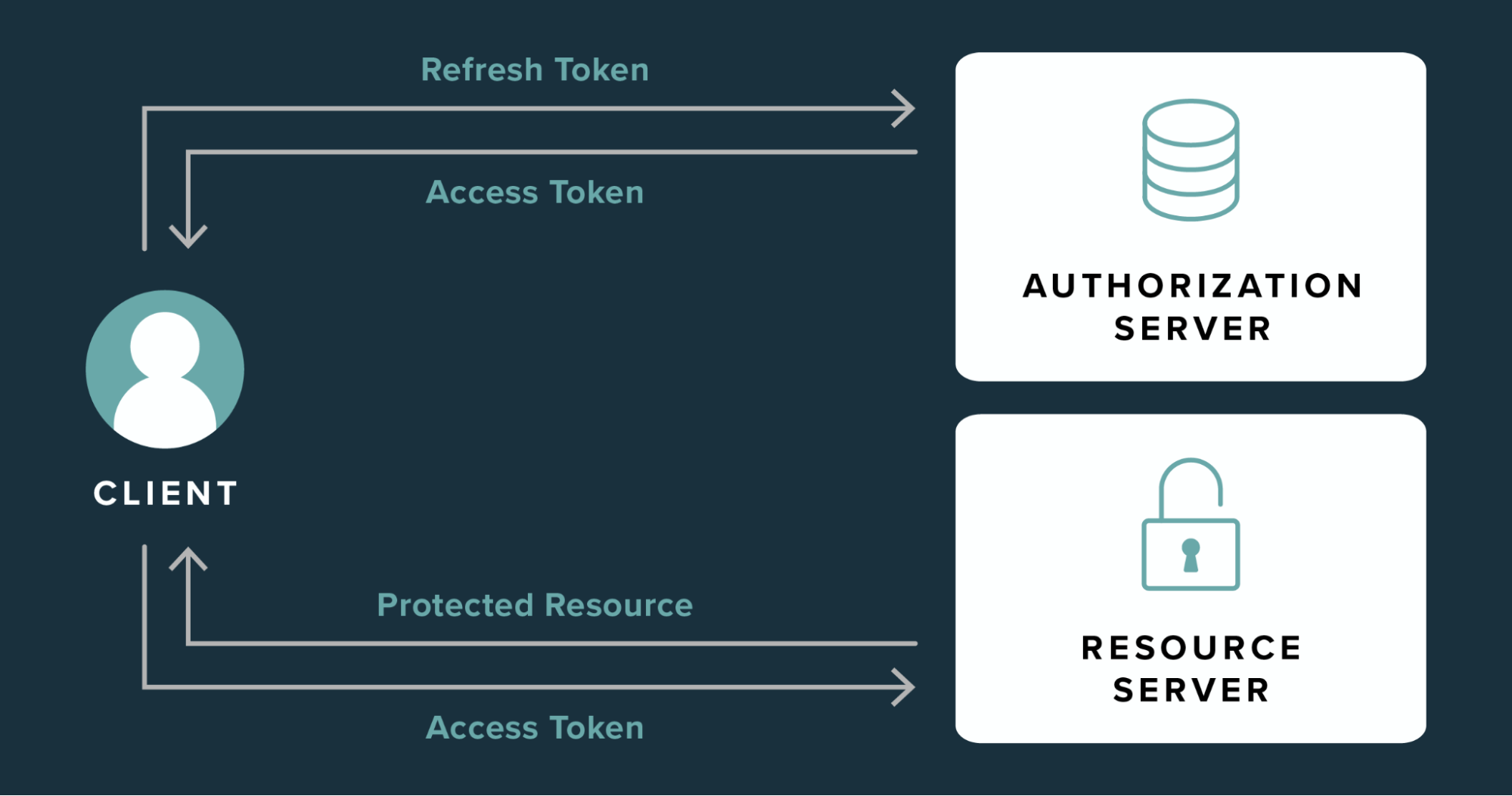
An access token serves as a digital key, enabling users to tap into devices, software, or other online utilities. The digital world today is populated with various token forms.
Physical Hardware Tokens
Physical hardware tokens are tangible devices that grant users access to specific resources. These tokens can be either connected directly, such as through USB ports or as smart cards, or operated wirelessly, like Bluetooth-enabled tokens. They were the forerunners in token-based authentication before smartphones became omnipresent. Their downside includes their higher costs, susceptibility to being lost or stolen, and a greater need for IT support due to these issues.
Digital Software Tokens
Soft tokens, or software tokens, offer a more contemporary and flexible approach. These tokens don’t require physical contact and can be employed from any location. Many of today’s software tokens manifest as mobile apps, utilizing smartphones for varied authentication layers like 2FA, MFA, or even JWTs. Their appeal lies in cost-effectiveness, increased convenience, minimized chances of misplacement, and a diminished risk of security breaches like man-in-the-middle attacks.
Unpacking JSON Web Tokens
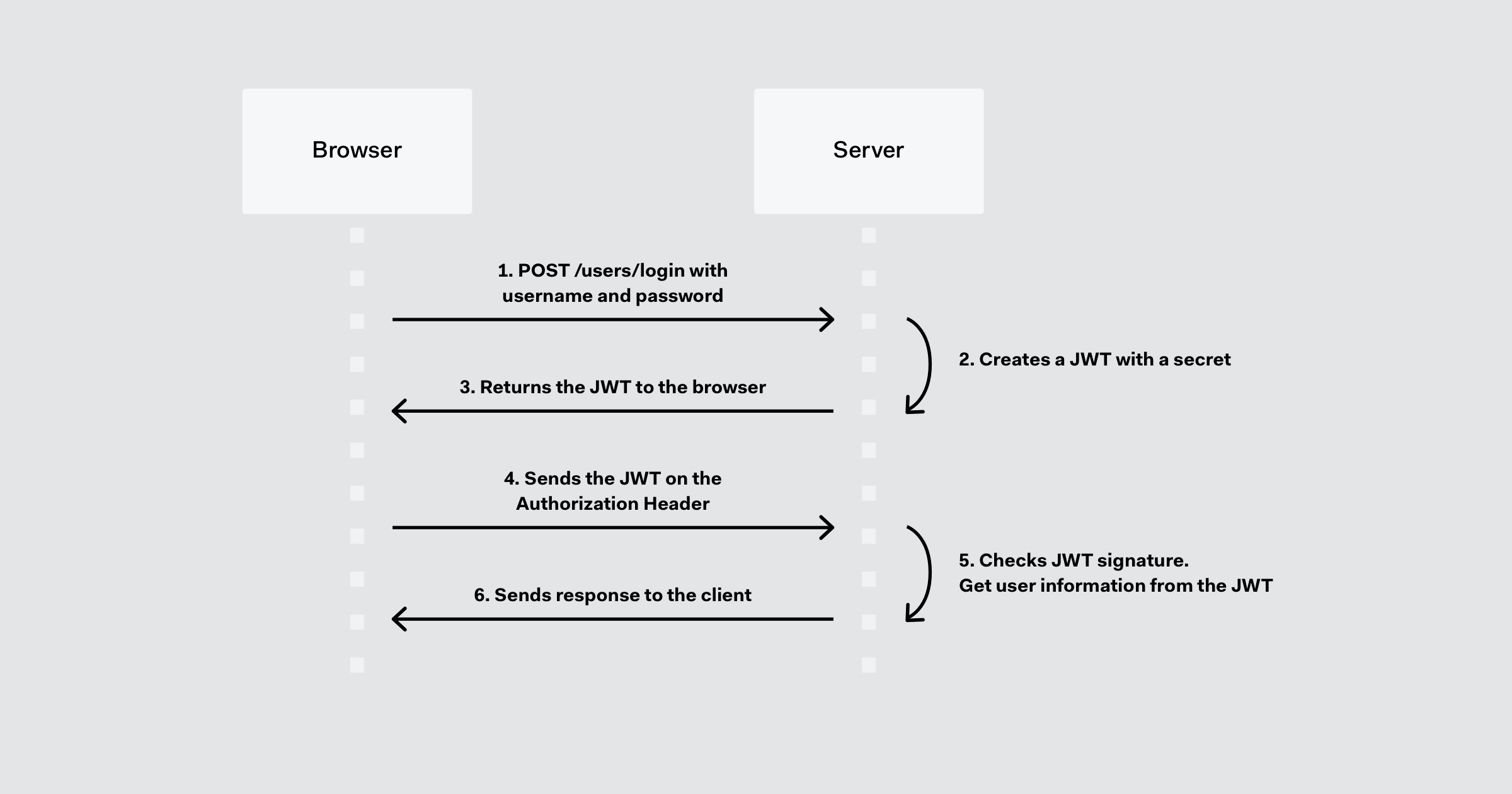
Among software tokens, JWTs or JSON Web Tokens are the frontrunners. JWTs are based on an open-source protocol (RFC 7519) that encapsulates information in a concise JSON object format, ensuring both security and efficiency during transmission. Their compact nature makes JWTs highly adaptable, fitting easily into URLs, headers, and POST request payloads.
Anatomy of a JSON Web Token
Every JSON web token splits into three distinct sections:
Header: It specifies the token’s kind and the encryption algorithm applied.
Payload: It houses the authentication information relevant to the desired resource.
Signature: A vital cryptographic component confirming the integrity of the payload.
Procedure to Implement Token-Based Authentication
Incorporating token-based authentication generally follows these steps:
User Entry: The user provides their login credentials.
Verification Phase: The central server validates the input credentials for correctness.
Token Generation: Upon successful verification, the server formulates a token with a defined duration.
Token Retention: The crafted token is stored in the user’s browser for future engagements.
Expiry Mechanism: Tokens operate within a predetermined duration, after which they cease to be active.
When is Token-Based Authentication Most Appropriate?
While conventional username-password pairs or server-side authentication may suffice for many applications, there are specific scenarios where the capabilities of token-based authentication shine brightly:
Intermittent Access Systems: For systems where user access constantly changes, such as those granting temporary rights, managing permissions becomes cumbersome with traditional methods. Tokens offer a dynamic approach to granting short-lived access, reducing administrative overhead.
Systems Demanding Fine-Grained Permissions: When your security model requires intricate access levels, such as permitting specific functions or document portions, simple password-based authentication falls short. Tokens allow for nuanced rights assignment and better monitoring by administrators.
High-Stakes Environments: Systems that store or process critical, confidential, or high-value information demand superior protective measures. Token-based authentication provides a more robust security layer than passwords alone.
Strictly Regulated Platforms: If your digital ecosystem holds information subject to stringent regulatory or compliance mandates, basic password protocols might not suffice. Token-based authentication, when configured correctly, aligns more closely with rigorous security standards.
Elevating Token-Based Authentication to its Peak
Despite the superiority of token-based authentication over traditional methods, it’s essential to recognize that tokens, especially bearer tokens, can still be vulnerabilities. If malicious entities acquire a token, they can impersonate its legitimate owner. Thus, it’s imperative to adopt and implement the following practices:
Prioritizing Token Privacy: It’s vital for users to treat tokens, irrespective of their physical or digital nature, as they would sensitive credentials. Store them securely, never disclose them recklessly, and ensure only authenticated services have access to them.
Optimizing Token Payloads: Tokens should encapsulate only the essential information required for user authentication. They’re not encrypted but encoded, meaning a motivated hacker can decode them. Consequently, avoid embedding confidential information within tokens and aim for payload minimalism, enhancing system responsiveness.
Establishing Token Lifespan and Recall Protocols: Though tokens typically become void after user logout or application termination, it’s fundamental to pre-define token lifetimes. Additionally, have a robust strategy in place for token invalidation when anomalies arise.
Mandating HTTPS Protocols: Given the ease with which data can be intercepted over unsecured connections, it’s paramount to transmit tokens over HTTPS channels, ensuring encryption and data integrity.
Layering Security Measures: Depending on the sensitivity and nature of your digital resources, consider integrating advanced security layers atop token-based authentication. For instance, an auxiliary token verification step can further validate the authenticity of token origin.



